SkyOnline + PwC Argentina
Double the Innovation in Cybersecurity
In cybersecurity, being obsessive is never too much. According to EY Spain, the global cost of cybercrime is estimated to reach $10.5 trillion annually by 2025. This poses a critical threat to large enterprises, whose infrastructures are constantly targeted by increasingly sophisticated technologies.
United to Deliver the Best Protection


Maximum security led us to form a strategic alliance with PwC Argentina, combining our expertise in technology infrastructure with PwC Argentina’s global leadership in risk management. Together, we deliver a cybersecurity service through our Security Operation Center (SOC), designed to protect assets 24/7, 365 days a year.
We work together to ensure companies are always protected

Immediate impact

Instant response

Active security

Our Comprehensive Security Services
Managed Detection and Response (MDR):
We continuously detect and respond to threats, minimizing the impact of cyberattacks.
Forensics:
In the event of a serious incident, we perform detailed forensic analysis to identify the root cause and prevent future vulnerabilities.
T RISK:
We assess, design, and implement tools for measuring and monitoring technological risks, ensuring your infrastructure is always aligned with best practices.
Security Framework:
We implement Information Security Management Systems (ISMS) based on international standards such as ISO 2700X, PCI-DSS, and NIST to ensure maximum protection.
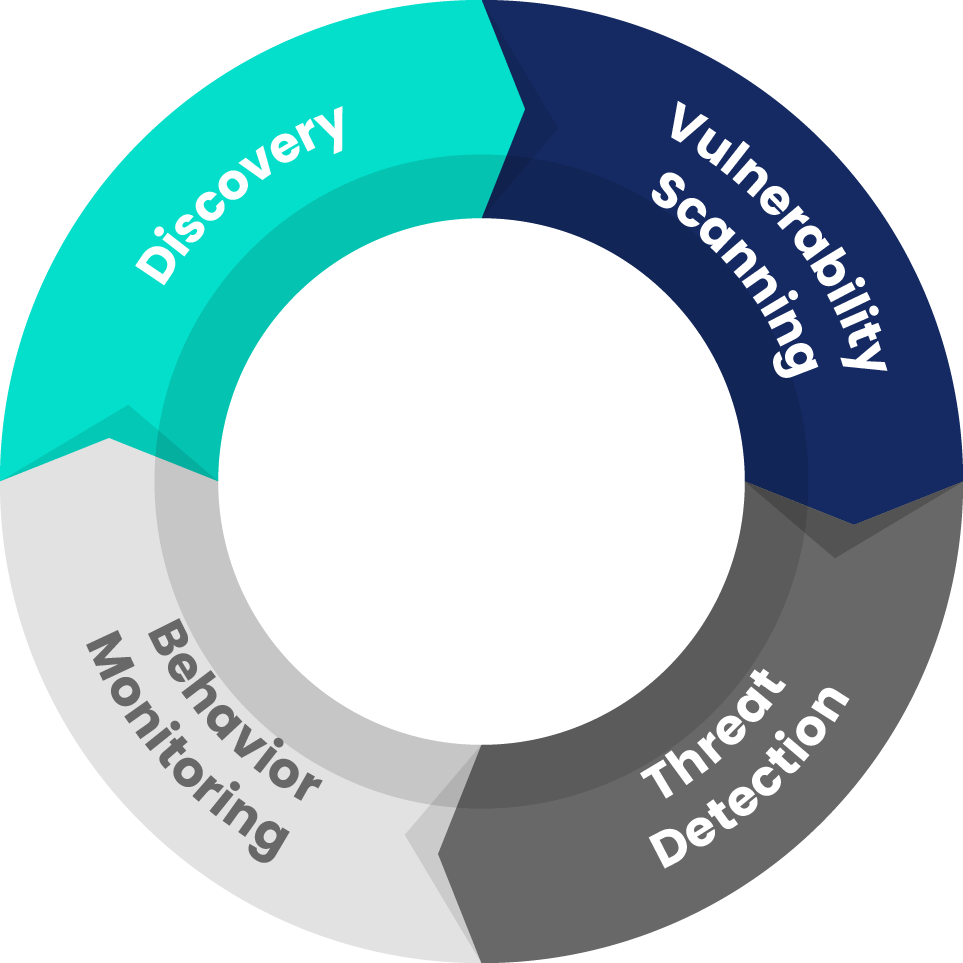
Vulnerability Scanning: Determines the “attack surface” and allows verification of compliance with standards.
Threat Detection: “Knowing” is key. Having updated correlation rules enables detection of new threats.
Behavior Monitoring: Establishing a behavioral baseline helps detect potential cyber attackers.
Your infrastructure protected by experts
Ethical Hacking
We identify and analyze vulnerabilities in web services and applications through controlled testing.
- Vulnerability Detection: We assess security flaws at various levels.
- Controlled Exploitation: We simulate attacks to measure their impact.
- Detailed Reporting: We provide reports with evidence and recommendations.
Hardening
We strengthen the security of your systems with optimized configurations.
- Best Practices: We implement cybersecurity standards.
- Customization: We tailor measures to your infrastructure.
- Application and Validation: We ensure effective protection.
Forensics
We analyze digital incidents following international protocols.
- Evidence Collection: We gather data with forensic validity.
- Chain of Custody: We ensure integrity and legal admissibility.
- Reporting and Certification: We provide detailed analyses and certifications.
ISAE 3402 Certification | Type 2
The ISAE (International Standard on Assurance Engagements) 3402 | Type 2 certification endorses reliable and secure management and operations.
Ethical Hacking
We identify and analyze vulnerabilities in web services and applications through controlled testing.
- Vulnerability Detection: We assess security flaws at various levels.
- Controlled Exploitation: We simulate attacks to measure their impact.
- Detailed Reporting: We provide reports with evidence and recommendations.
![]()
Hardening
We strengthen the security of your systems with optimized configurations.
- Best Practices: We implement cybersecurity standards.
- Customization: We tailor measures to your infrastructure.
- Application and Validation: We ensure effective protection.
![]()
Forensics
We analyze digital incidents following international protocols.
- Evidence Collection: We gather data with forensic validity.
- Chain of Custody: We ensure integrity and legal admissibility.
- Reporting and Certification: We provide detailed analyses and certifications.
![]()
ISAE 3402 Certification | Type 2
The ISAE (International Standard on Assurance Engagements) 3402 | Type 2 certification endorses reliable and secure management and operations.
